Самое актуальное и обсуждаемое
Популярное
Полезные советы

Важно знать!
10 удивительных фактов об овсяной каше, её польза и способы приготовления
Полезные свойства овсяных хлопьев
Овсянка – отличный источник полисахаридов, или так называемых «медленных» углеводов. Такие вещества помогают человеку сохранить энергию на длительное время после еды,...
Читать далее
12 простых рецептов приготовления желе из вишни на зиму
5 вкусных и простых рецептов приготовления куриного филе в соусе
10 продуктов, в которых кальция больше, чем в твороге
5 блюд, которые получаются из телятины лучше, чем из говядины
5 способов применения оливкового масла в медицине
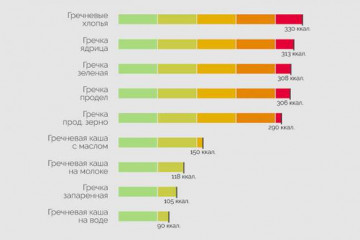
12 продуктов, богатых железом (среди них гречка и яйца)
27 лучших рецептов приготовления варенья из груш на зиму в домашних условиях
10 продуктов, которые сгущают кровь. с чем быть осторожнее?
3 рецепта домашнего кваса из хлеба на живых дрожжах
Лучшее

Важно знать!
10+ беспроигрышных рецептов приготовления морепродуктов на сковороде
Ингредиенты
Морской коктейль: 400 г
Помидор большой: половина
Лук репчатый: 1 шт.
Чеснок: 4 дольки
Петрушка: 4 веточки
Растительное масло: 3 ст. л.
Красный отсрый перец: 2 щепотки
Соль: по вкусу
Как...
Читать далее
16 уникальных свойств кедрового масла, о которых вы не знали
11 лучших сортов тыквы
7 рецептов хреновухи на водке в домашних условиях
7 простых рецептов очень вкусных котлет из горбуши
5 интересных рецептов кофе с корицей, а также полезные свойства напитка
8 фактов о суши, о которых вы не задумывались
20 куриных супов для тех, кто любит вкусно поесть
20 экзотических фруктов, о которых мы ничего не знали
7 пошаговых рецептов компота из апельсинов на зиму, как сварить в домашних условиях и хранение заготовки
Обсуждаемое

Важно знать!
14 лучших сортов черевишни: описание и фото, отзывы садоводов
Общее описание сливово-вишневого гибрида
Смесь сливы и вишни под названием СВГ — это садовое растение, приносящие свой первый урожай уже на 2 – 3 год жизни. Сливо-вишневый гибрид успешно сочетает в себе...
Читать далее
20 экзотических фруктов, о которых вы ничего не знали
100 грамм сливочного масла
7 лучших производителей масла черного тмина
10 интересных фактов о лимонаде
15 лучших рецептов алкогольного пунша, которые не оставят вас равнодушным!
11 красных ягод, которые вам необходимы
7 причин есть манго чаще
4 варианта диеты на гречке и вкусные рецепты для желающих похудеть
2 простых и вкусных рецепта компота из фиников
Актуальное

Важно знать!
5 рецептов, как вкусно сварить мороженные креветки в домашних условиях с фото
Хрустящие и аппетитные жаренные креветки
Жареные креветки к пиву
— один из самых популярных домашних снеков. Приготовить их возможно разными
способами.
Базовый рецепт:
размораживаем
ракообразных и чистим...
Читать далее
12 способов использовать кукурузный крахмал
5 полезных каш: медленные углеводы на страже здоровья
11 полезных свойств ромашкового чая
4 нехитрых способа определения свежести яиц в домашних условиях
29 природных афродизиаков для мужчин: никаких таблеток и тот же эффект
15 способов использовать спирт
3 отличия карпа от сазана
13 популярных сортов декоративного лука с описанием
6 способов замариновать свиные ребра для жарки в духовке
Обновления
 Статьи
Секреты вкусного шашлыка: выбор мяса и маринада для идеального результатa!
Статьи
Секреты вкусного шашлыка: выбор мяса и маринада для идеального результатa!
В мире кулинарии, искусство приготовления шашлыка занимает особое место, и выбор правильного мяса и...
 15 топ сорняков, которые часто растут на участке
15 топ сорняков, которые часто растут на участке
Как избавиться от травы механическим способом
Сенна трава: описание, где растет, свойства и применение
Если...
 6 вкусных альтернатив сыру пекорино романо
6 вкусных альтернатив сыру пекорино романо
Но что же сделало всемирно известным именно Романо
Начнем с того, что это единственный сыр, который...
 19 рецептов варенья из апельсинов
19 рецептов варенья из апельсинов
Способы приготовления
Истинные гурманы оценят богатство вкусов и аромат готового лакомства. Наиболее...
 13 рецептов шашлыка из индейки на мангале
13 рецептов шашлыка из индейки на мангале
Особенности подачи на стол?
Шашлык – самое ожидаемое блюдо на застолье и пикнике. Поэтому его нужно...
 10 лучших рецептов из мяса камчатского краба
10 лучших рецептов из мяса камчатского краба
Как правильно есть
Обычно разделать краба не так легко, особенно когда пробуешь это впервые, но с волосатиком...
 10 рецептов домашней выпечки из рисовой муки. как сделать тесто, чтобы оно было вкусным?
10 рецептов домашней выпечки из рисовой муки. как сделать тесто, чтобы оно было вкусным?
Полезные и лечебные свойства рисовой муки
Польза продукта обусловлена содержанием значительного количества...
 12 рецептов рыбы на мангале для настоящих гурманов
12 рецептов рыбы на мангале для настоящих гурманов
рецепт рыбы на мангале
От теории пора переходить к практике, а чтобы вам было легче, рассмотрим простые...
 9 фактов, которые нужно знать о замене моторного масла
9 фактов, которые нужно знать о замене моторного масла
Растительное масло и его полезные альтернативы
Те, кто любят различные салаты, знают как масло может...
 6 продуктов питания для здоровья женской груди
6 продуктов питания для здоровья женской груди
5.Грейпфрут
Помимо того, что грейпфрут – продукт диетический и часто включающийся во всевозможные женские...
 7 самых вкусных датских сладостей
7 самых вкусных датских сладостей
Брунсвир (Brunsviger)
В 170 км от Копенгагена есть датский остров Фюн. Он прославился на весь мир тем,...
 14 полезных цельнозерновых продуктов (включая безглютеновые)
14 полезных цельнозерновых продуктов (включая безглютеновые)
Рожь
Это зимостойкое озимое растение. Зерна ржи длиннее, чем пшеницы. Цвет плода может быть коричневым,...